Deploying DetectX Swift with Munki
DetectX Swift is an alternative to MalwareBytes Anti-Malware and was more economical for our district to use. It also is faster and more what we were looking for. I highly recommend it! This is a write up based on how we are deploying it here.
First things first, if you are reading this, you will need a Management License from Sqwarq for DetectX Swift; Cost is $299 USD. Once you have this, make note of the information in the email with the account information.
We decided to deploy it to /Applications/Utilities. This makes it still easy to access but out of the standard users view. We deploy it via Munki as well. You will also need to add a post-install script to register the client. Thankfully DetectX Swift allows for re-registering with no issue, so you can "register" it after every installation. Here is the pkginfo dict for the autopkg recipe:
<key>pkginfo</key>
<dict>
<key>catalogs</key>
<array>
<string>testing</string>
</array>
<key>description</key>
<string>DetectX Swift is a shareware security and troubleshooting tool that uses a combination of hardcoded search definitions along with live updates and predictive heuristics to detect both known and unknown threats and issues. It provides the user with multiple analytical capabilities regarding both the system’s current state and changes to its state over time related to its ongoing security and performance.</string>
<key>category</key>
<string>Utlities</string>
<key>developer</key>
<string>Philip Stokes</string>
<key>display_name</key>
<string>DetectX Swift</string>
<key>name</key>
<string>%NAME%</string>
<key>unattended_install</key>
<true/>
<key>items_to_copy</key>
<array>
<dict>
<key>destination_path</key>
<string>/Applications/Utilities</string>
<key>source_item</key>
<string>DetectX Swift.app</string>
</dict>
</array>
<key>minimum_os_version</key>
<string>10.11</string>
</dict>
<key>postinstall_script</key>
<string>#!/bin/bash
"/Applications/Utilities/DetectX Swift.app/Contents/MacOS/DetectX Swift" register -key "KEYNUMBER" -email "REGISTEREDEMAIL"
"/Applications/Utilities/DetectX Swift.app/Contents/MacOS/DetectX Swift" search -aj "/usr/local/munki/preflight.d/cache/detectx.json"
</string>
If you are using MunkiReport-PHP, there is a module I created in the current WIP branch. WIP is not stable for production, but should be entering beta soon. In order to use the module you will need to create a launchDaemon targeting DetectX Swift's CLI tool to output a JSON file. There is an example in the module READMD file.
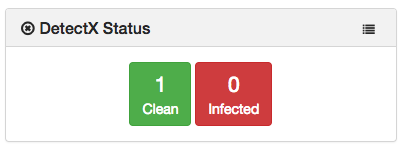
I am deploying a boot-every script with Outset that does the same thing. I packaged this up as an update_for in Munki. This will provide a dashboard that will give you in-depth look at the current status of your fleet. The client tab will show you exactly what each client shows for each infection. The command structure for this is as follows:
#!/bin/bash
"/Applications/Utilities/DetectX Swift.app/Contents/MacOS/DetectX Swift" search -aj "/usr/local/munki/preflight.d/cache/detectx.json"
This will scan (if you are running it independently you must run it as root!) all users homes and report on it's findings. It is fairly quick. If you combine all of this together you get an auto-updating anti-malware solution that reports to a dashboard for every machine you deploy it too. If there are machines supsected of having malware, we call the employee and request they do a quick restart so that the boot-every script has a chance to report, then perform a Munki update check to send the data to us. So far this has proven effective and useful here.